It is important to have some background information about how the sudo command operates and how it can be configured before we hit the vulnerability. When you execute commands on a Linux operating system, unprivileged users can use the sudo (super user) command to execute root commands as long as permission is given or root user password is known. The sudo command can also be set to allow a user to execute commands as a separate user by adding special directives to the /etc / sudoers configuration directory. In the following commands, for example, user “test” may run the commands /usr / bin / vim and /usr / bin / id, as any user but root. To execute the “check” user, a sudo command with the -u argument would be used to signify the client to execute it. The following instruction, for example, will begin vim as the ‘ bleeping-test ‘ user. That user is given a UID when creating Linux apps. As shown below, the user ‘ check’ has a UID of 1001 and a UID of 1002 is available for’ bleep-test.’
UIDs of users The sudo feature allows users to use these UIDs instead of a password. For example, the command below will restart VIM as a “bleeping-test,” but this time by providing the UID of the client.
The Weakness of the Sudo
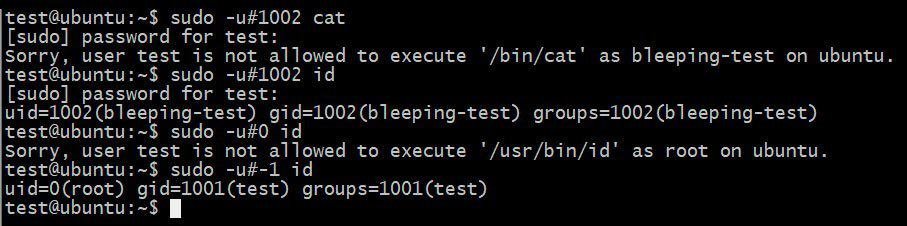
A vulnerability of Apple Security researcher Joe Vennix has been discovered that allows users to launch an approved sudo command as root using the sudo command-1 or 4294967295 UID. The following instruction, for instance, could use this bug to run the /usr / bin / id user, even if the “check” user was denied it in the /etc / sudoers file. The following is explained with this bug with the /usr / bin / id command to gain root privileges.
Using the sudo bug to run /usr/bin/id as root While this is a powerful feature, it is important to remember that it can only operate if the configuration file of sudoers allows a user access to an order. If not, and most Linux distributions are not default, this bug will have no effect.
Development of an Assault
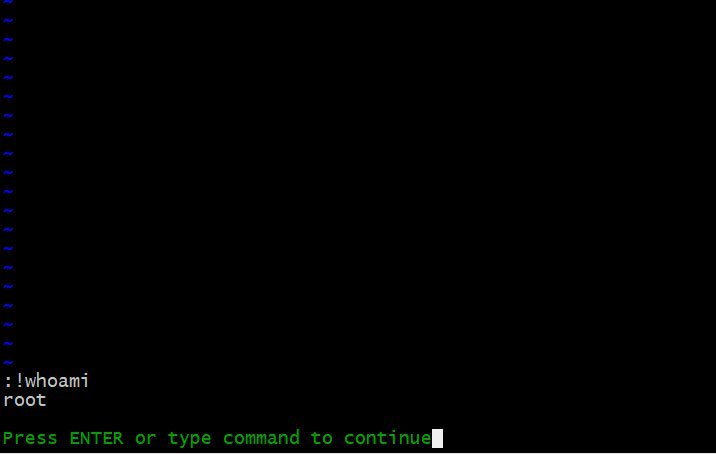
To effectively use this weakness, a client would have to have a sudoer directive configured to launch other commands. We have such a command in our example sudoers instructions above, the VIM command! In VIM, a user could start a different program using the:! Order. Command. For example, if you can enter in VIM!In the current directory, ls to execute the ls instruction. If we use sudo-u#-1 vim to use this vulnerability, VIM is launched as user. It can then be checked by running the!The order of whoami.
VIM running as root Now that VIM is launched as root, all commands executed are also launched as root. This can easily be used to open a root shell to execute any command on the affected machine. This assault is shown in the following video.
Launching a root shell Although this bug is obviously strong, it can only be used in non-standard configurations that do not affect most Linux users. You must update to sudo 1.8.28 as soon as possible for those who use sudoer directives for your applications.